Our Instructors Collaborate With Top Tech Leaders
 Startups
Startups

 Microsoft
Microsoft
 NVIDIA
NVIDIA
Build a smart security solution using YOLOv7 to detect
unauthorized human entry in restricted zones. Learn real-time
detection and automatic alert generation.
Intermediate-level. Certificate included.
 Startups
Startups

 Microsoft
Microsoft
 NVIDIA
NVIDIA
By the end of this course, you'll have the skills to build AI-powered accident detection systems and secure computer vision jobs or freelance projects.
Explore how AI and vision systems detect unauthorized human entry in restricted areas.
Utilize Python with OpenCV and deep learning models like YOLO for intrusion detection.
Build a real-time monitoring system to identify and alert on intruder presence.
Record intrusion events with timestamps into a database for review and security reporting.
Create a GUI to view live footage and receive real-time intrusion alerts.
Finish the course and receive a verified certificate of success.

Muhammad Yaqoob is the founder of Tentosoft Pvt Ltd and a seasoned Computer Vision expert. With 10+ years of experience and over 5,000+ students taught globally, he brings deep industry knowledge and a passion for practical, hands-on learning.
Gain practical experience by building industry-relevant computer vision applications from scratch.

This section provides an overview of how human intrusion detection works using computer vision and AI. It introduces the real-world applications of detecting unauthorized human entry into restricted areas and outlines how models like YOLOv7 can be used to recognize and respond to such events in real time.
Course Overview and Features
AI-Powered Intrusion Detection Overview
Project Scope and Real-World Applications
Setting up Python and its development tools is the foundation of building AI applications. This ensures the environment is ready to run and develop object detection models.
Installing Python
VS Code Setup for Python Development
This section teaches you how to launch Visual Studio Code directly from the command line (CMD). It helps streamline your development workflow by enabling quick access to project directories and files without navigating through the interface manually.
Understanding Key Packages for Intrusion Detection System
Start Visual Studio Code via Command Line
Set up the full environment to support smooth AI model execution.
This part ensures that all software dependencies are correctly installed, including deep learning and computer vision packages.
Understanding Key Packages for Intrusion Detection System
Setting Up Virtual Environment
Adding Computer Vision Support
Handling Package Conflicts and Errors
Learn how polygons are used to define custom detection zones, enabling more advanced tracking and analysis in defined areas.
Polygon Coordinate File Access and Parsing
Polygon Coordinate File Access and Parsing
Mapping Coordinates to Video Frames
Multiple Polygon Zone Support

Explore how internal parameters influence model behavior, helping you customize YOLOv7 for better control and fine-tuning.
Understanding and Customizing Key Variables in YOLOv8
Confidence Threshold Setting
Confidence and IoU in Fine-Tuning

This applies the detection model specifically for security and intrusion use cases, analyzing movement across boundaries or restricted areas.
Model Inference Code Explanation for Intrusion Detection
Loading the Trained Detection Model
Triggering Alerts or Logging Events
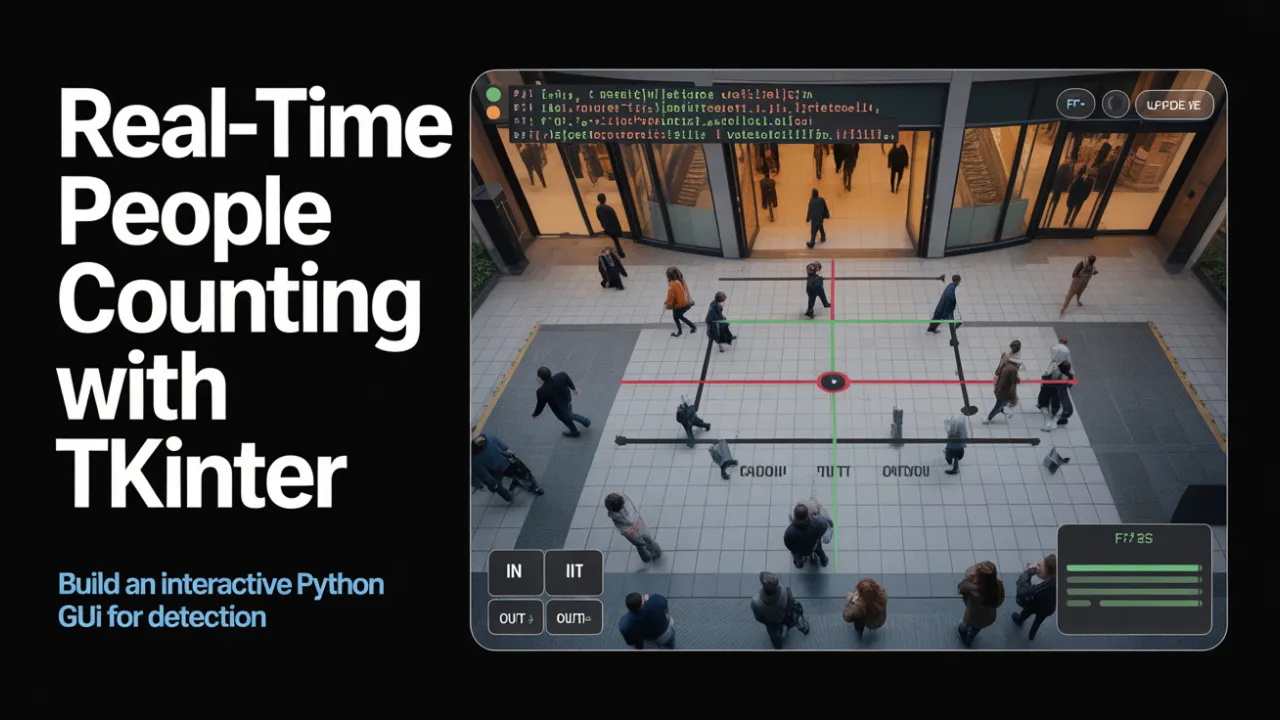
This section demonstrates how to integrate intrusion detection functionality into a Tkinter-based GUI. It focuses on connecting real-time object tracking with custom detection zones, enabling live monitoring and alerting through an interactive desktop interface.
Tkinter Implementation for Real-Time Intrusion Detection
Setting Up the Tkinter Window Layout
Displaying Intrusion Alerts in Real-Time
Saving Intrusion Logs from GUI
Is This Course Right for You?
Kickstart your AI journey with structured, hands-on learning.
Build a portfolio that recruiters can't ignore.
Add powerful AI/CV features to your apps and software.
Upskill for higher-paying, future-ready tech roles.
Build Smarter, more intelligent applications.
Transition into AI even with zero background.
One-time payment for lifetime access to all course materials and updates
Get hands-on experience with real-world projects designed to sharpen your technical skills and build your confidence. Each project is crafted to help you apply concepts practically, write cleaner code, and prepare for real developer challenges.
Highly recommended for small teams who seek to upgrade their time & perform.
₹ 6720 inclusive of GST ₹ 13999
52% OFF🎁 Coupon Code:
Secure Payment Gateway


You can add this certificate in your Resume! Share it with your LinkedIn network 🚀

Get full project code for 20+ real-world applications – build, customize, and learn hands-on with working solutions.
Join weekly live Q&As to resolve queries and deepen your understanding with real-time support
Enhance your confidence with communication tips, resume builder templates, and personal branding guides tailored for tech careers.
Get feedback, share wins, and grow with other learners in a safe and supportive environment.
Enroll today to claim all bonuses before the offer expires!
Get Instant Access